From Visibility to Resilience: Rethinking OT Security in a Converged World
Operational Technology (OT) environments underpin critical infrastructure: from water management and transport to energy distribution and manufacturing. Increasingly interconnected with IT networks, these systems face a rapidly evolving cyber threat landscape. At Fox-IT, we believe securing OT is not just about buying tools. It requires a layered, context-driven monitoring approach that blends proven IT capabilities with OT-specific measures, while maximising existing investments.
Beyond Point Solutions
A common misconception is that deploying a network sensor alone is sufficient for OT monitoring. While passive sensors, capable of deep packet inspection, are invaluable, they form just one element of a broader framework. Fox-IT uses an iterative process, starting with asset inventory, classification, and architecture design, before adding detection capabilities.
This ensures monitoring is not technology-first but part of an end-to-end model spanning segmentation, recovery, 24/7 Security Operations Center (SOC) monitoring, and incident response. In practice, water authorities often classify treatment facilities as “no-failure” environments, requiring strict segmentation and full SOC coverage, while public lighting networks are treated as medium-criticality, allowing lighter monitoring.
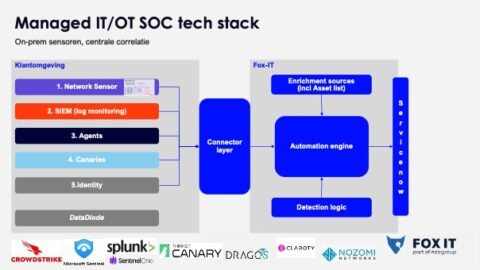
The OT Monitoring Stack: A Layered View
An effective OT monitoring stack combines complementary layers:
- Network Sensors: Still the cornerstone, as passive monitoring has no impact on sensitive environments. Our Fox NDR sensor, often paired with specialist partner tools, also stores PCAPs for threat hunting. In one deployment, passive sensors uncovered undocumented PLCs at pumping stations, helping prioritise segmentation and monitoring.
- SIEM & Log Monitoring: Firewall and authentication logs provide context sensors alone cannot. Integrating OT logs into SIEM creates a unified IT/OT view.
- Endpoint & Host-Based Defences: Increasingly viable in OT, adding defence against lateral movement and ransomware.
- Deception & Early Warning: Canary tokens and decoys detect intrusions early, especially at the IT/OT boundary.
- Identity & Access Monitoring: Privileged access remains a key attack vector. Monitoring and enforcing strict access models is critical.
- Data Diodes & Segmentation: Hardware-enforced one-way communication ensures safe data flow without exposing critical systems.
- Threat Intelligence & Use Case Development: Detection logic must adapt continuously to sector-specific threats.
Together, these layers deliver visibility and resilience across the full spectrum of IT and OT threats.
Greenfield vs. Brownfield: Pragmatic Application
In greenfield projects, security can be designed in from the outset: segmentation, data diodes, and integrated monitoring.
In brownfield environments however, legacy systems and constraints limit options. Tunnel control systems, for instance, often run on decades-old protocols and cannot be patched. Here, layered monitoring and strict access control provide resilience without costly replacement.
Our iterative approach offers a roadmap:
- Start with asset visibility
- Leverage existing investments (SIEM, EDR) before adding tools
- Prioritise based on criticality
This ensures cost-effectiveness while steadily raising the baseline.
The Role of the SOC: More Than Alert Forwarding
Technology is only half the story. An effective IT/OT SOC must go beyond forwarding alerts. Analysts need contextual knowledge of OT processes, the ability to triage against physical impacts, and the capacity to collaborate with operational teams.
We have seen SOC analysts trained in both IT and OT distinguish between a genuine malware infection and a scheduled SCADA reboot, avoiding unnecessary downtime. At Fox-IT, this expertise is embedded in our global SOC, supported by the Unified Cyber Platform, which integrates IT and OT data streams and enables flexible use of client investments.
Fox-IT has a long legacy in pioneering SOC solutions, from operating the first SOC in Europe to building the first integrated IT/OT SOC with a cohesive Digital Forensics and Incident Response function.Conclusion
“You can’t stop what you can’t see.” Visibility remains the cornerstone of OT security, but it must be built as part of a layered stack. By combining network detection, SIEM, host defences, deception, identity monitoring, segmentation, and threat intelligence, organisations can achieve sustainable resilience.
Whether greenfield or brownfield, the goal is not to adopt every technology at once. The future of OT monitoring lies in maximising existing investments, closing gaps pragmatically, and embedding monitoring in a broader IT/OT SOC framework.
Fox-IT and NCC Group stand ready to support organisations on this journey, ensuring OT environments remain both secure and operational in the face of evolving threats..
CLIENT SPOTLIGHT (link to original case study)
Enhancing OT Security in Industrial Manufacturing
A European precision machinery manufacturer with 5,000+ employees faced growing cyber threats, legacy OT vulnerabilities, and rising regulatory pressure. With overstretched internal teams and limited visibility across production sites, the company partnered with NCC Group and Fox-IT to strengthen resilience.
The engagement began with a full assessment, which revealed poor IT/OT segmentation, outdated assets, and patching gaps. NCC Group introduced a layered programme: 24/7 SOC monitoring across IT and OT, tailored industrial threat intelligence, and automated response playbooks. OT-specific defences, including segmentation, industrial firewalls, and strict access controls, were deployed without disrupting production, while targeted training and continuous vulnerability management embedded long-term resilience.
Business Outcomes
- Faster response: Incidents contained in hours instead of days.
- OT resilience: No major OT incidents in 12 months.
- Compliance: Achieved ISO/IEC 27001, improving customer trust.
- Stronger culture: Fewer phishing successes, more incident reporting.
- Operational efficiency: Internal teams freed for strategic projects.
Key Lesson: By involving OT teams early, NCC Group and Fox-IT ensured security strengthened resilience without hindering operations.
Register for free for Cybersec Netherlands 2025
As cyber attacks continue to threaten today’s tech landscape, this event is the premier platform for seasoned cyber security professionals and innovative start-ups to exchange knowledge and tackle cybersecurity challenges together. Organizations across all sectors will discover strategies to boost cyber resilience and safeguard critical assets. Don’t miss this chance to strengthen your cyber defenses—register for free now!












